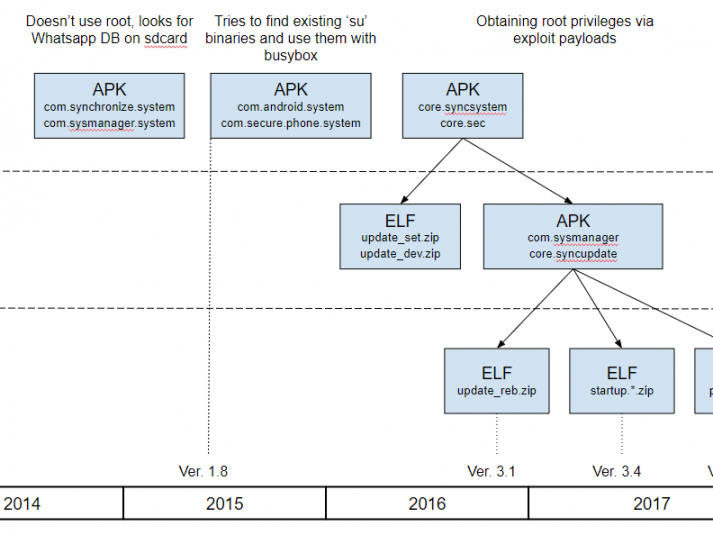
At the beginning of October 2017, was discovered new Android spyware with several features previously unseen in the wild. In the course of further research, it was found a number of related samples that point to a long-term development process. They believe the initial versions of this malware were created at least three years ago – at the end of 2014. Since then, the implant’s functionality has been improving and remarkable new features implemented, such as the ability to record audio surroundings via the microphone when an infected device is in a specified location; the stealing of WhatsApp messages via Accessibility Services; and the ability to connect an infected device to Wi-Fi networks controlled by cybercriminals.
It was observed many web landing pages that mimic the sites of mobile operators and which are used to spread the Android implants. These domains have been registered by the attackers since 2015. According to our telemetry, that was the year the distribution campaign was at its most active. The activities continue: the most recently observed domain was registered on October 31, 2017. Based on our KSN statistics, there are several infected individuals, exclusively in Italy.
Moreover, as they dived deeper into the investigation, we discovered several spyware tools for Windows that form an implant for exfiltrating sensitive data on a targeted machine. The version we found was built at the beginning of 2017, and at the moment we are not sure whether this implant has been used in the wild.
It was named the malware Skygofree, because we found the word in one of the domains*.
How to protect yourself against it?
As the popularity of smartphones increases, so does the number of attacks destined to these platforms. “If you would like to develop espionage tools, mobiles will always be in the front line,” maintains the analyst of the Russian firm, for whom the main reason is that “we all use them”. But there is another: “we do not know how to protect ourselves.”
The malwares are usually designed to go unnoticed and that a common user can not see them. The situation is still complicated if, as in smartphones, the manufacturers themselves can not keep track of malicious applications. “You must have a technical level to know how to look for traces of suspicious things, or some kind of protection that does that work for you,” says Díaz. The level of opacity increases in more closed systems, such as iOS: “you have to put your faith that the seller will protect you from everything”, says the specialist.
Therefore, the manufacturers themselves have made sure to develop protection mechanisms that, although efficient, are still not totally safe. Android also has an added problem: fragmentation. Each device belongs to a company, and each one is compatible with a version of the system. The consequences? That more than 1,000 million gadgets are outdated.
According to them, “there are already patches for many of the vulnerabilities exploited by Skygofree”, but these have not reached the entire Android market. Even so, according to the expert, the most current versions should be able to, at least, “mitigate their capacity” by restricting their access to administrator tasks.
Although the protection against such threats largely corresponds to security companies, users can also prevent them by making conscious use of the device. As Kaspersky recommends, you have to “be careful” with unknown emails, attachments, and check the origin of the websites before entering the links.
Likewise, it is also advisable to have the latest version of the operating system installed and to be prevented from applications downloaded from Google Play, the official apps store. In the end, it is about putting all possible barriers between the attacker and the user so that the malware falls into one of them, either by a patch or by an antivirus. “Everything that helps, well, it’s welcome,” says Díaz.
Find more information about it here: https://securelist.com/skygofree-following-in-the-footsteps-of-hackingteam/83603/